adnanthekhan.com/2024/01/10/cve-2023-49291-and-more-a-potential-actions-nightmare
Preview meta tags from the adnanthekhan.com website.
Linked Hostnames
15- 8 links togithub.com
- 7 links toadnanthekhan.com
- 2 links towww.paloaltonetworks.com
- 1 link toapi.whatsapp.com
- 1 link tocve-2023-49291
- 1 link tofacebook.com
- 1 link togohugo.io
- 1 link tonews.ycombinator.com
Thumbnail
Search Engine Appearance
CVE-2023-49291 and More - A Potential Actions Nightmare
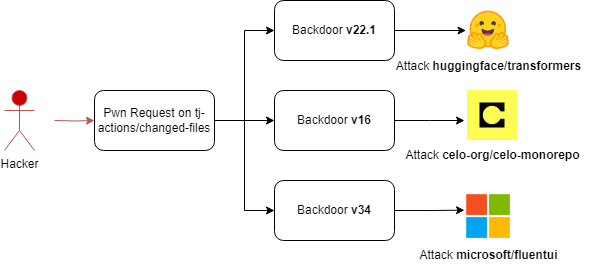
Introduction I’ve been doing a lot of scanning and reporting of GitHub Actions injection and pwn request vulnerabilities throughout GitHub. Most of my scanning and testing focused on workflows - that is yaml files in the .github/workfows directory - and my regexes didn’t look at files in other directories, such action.yml, which is used as the entry-point for any repository that functions as a reusable GitHub Action. At Defcon Asi Greenholts and his team from Palo Alto Networks outlined the risk of a compromise of a reusable GitHub Action and how an attacker can exploit an action for an initial foothold, and then poison specific tags in order to target other actions and repositories. That talk had me think about looking for issues in reusable actions themselves.
Bing
CVE-2023-49291 and More - A Potential Actions Nightmare
Introduction I’ve been doing a lot of scanning and reporting of GitHub Actions injection and pwn request vulnerabilities throughout GitHub. Most of my scanning and testing focused on workflows - that is yaml files in the .github/workfows directory - and my regexes didn’t look at files in other directories, such action.yml, which is used as the entry-point for any repository that functions as a reusable GitHub Action. At Defcon Asi Greenholts and his team from Palo Alto Networks outlined the risk of a compromise of a reusable GitHub Action and how an attacker can exploit an action for an initial foothold, and then poison specific tags in order to target other actions and repositories. That talk had me think about looking for issues in reusable actions themselves.
DuckDuckGo
CVE-2023-49291 and More - A Potential Actions Nightmare
Introduction I’ve been doing a lot of scanning and reporting of GitHub Actions injection and pwn request vulnerabilities throughout GitHub. Most of my scanning and testing focused on workflows - that is yaml files in the .github/workfows directory - and my regexes didn’t look at files in other directories, such action.yml, which is used as the entry-point for any repository that functions as a reusable GitHub Action. At Defcon Asi Greenholts and his team from Palo Alto Networks outlined the risk of a compromise of a reusable GitHub Action and how an attacker can exploit an action for an initial foothold, and then poison specific tags in order to target other actions and repositories. That talk had me think about looking for issues in reusable actions themselves.
General Meta Tags
13- titleCVE-2023-49291 and More - A Potential Actions Nightmare | Adnan Khan's Blog
- charsetutf-8
- X-UA-CompatibleIE=edge
- viewportwidth=device-width, initial-scale=1, shrink-to-fit=no
- robotsindex, follow
Open Graph Meta Tags
7- og:urlhttps://adnanthekhan.com/2024/01/10/cve-2023-49291-and-more-a-potential-actions-nightmare/
- og:site_nameAdnan Khan's Blog
- og:titleCVE-2023-49291 and More - A Potential Actions Nightmare
- og:descriptionIntroduction I’ve been doing a lot of scanning and reporting of GitHub Actions injection and pwn request vulnerabilities throughout GitHub. Most of my scanning and testing focused on workflows - that is yaml files in the .github/workfows directory - and my regexes didn’t look at files in other directories, such action.yml, which is used as the entry-point for any repository that functions as a reusable GitHub Action. At Defcon Asi Greenholts and his team from Palo Alto Networks outlined the risk of a compromise of a reusable GitHub Action and how an attacker can exploit an action for an initial foothold, and then poison specific tags in order to target other actions and repositories. That talk had me think about looking for issues in reusable actions themselves.
- og:localeen-us
Twitter Meta Tags
4- twitter:cardsummary_large_image
- twitter:imagehttps://adnanthekhan.com/wp-content/uploads/2024/01/tj_chain.png
- twitter:titleCVE-2023-49291 and More - A Potential Actions Nightmare
- twitter:descriptionIntroduction I’ve been doing a lot of scanning and reporting of GitHub Actions injection and pwn request vulnerabilities throughout GitHub. Most of my scanning and testing focused on workflows - that is yaml files in the .github/workfows directory - and my regexes didn’t look at files in other directories, such action.yml, which is used as the entry-point for any repository that functions as a reusable GitHub Action. At Defcon Asi Greenholts and his team from Palo Alto Networks outlined the risk of a compromise of a reusable GitHub Action and how an attacker can exploit an action for an initial foothold, and then poison specific tags in order to target other actions and repositories. That talk had me think about looking for issues in reusable actions themselves.
Link Tags
7- apple-touch-iconhttps://adnanthekhan.com/apple-touch-icon.png
- canonicalhttps://adnanthekhan.com/2024/01/10/cve-2023-49291-and-more-a-potential-actions-nightmare/
- iconhttps://adnanthekhan.com/favicon.ico
- iconhttps://adnanthekhan.com/favicon-16x16.png
- iconhttps://adnanthekhan.com/favicon-32x32.png
Website Locales
1en
https://adnanthekhan.com/2024/01/10/cve-2023-49291-and-more-a-potential-actions-nightmare/
Links
29- http://CVE-2023-49291
- https://adnanthekhan.com
- https://adnanthekhan.com/about
- https://adnanthekhan.com/archives
- https://adnanthekhan.com/cdn-cgi/l/email-protection