blog.redsift.com/cybersecurity/wannacry-attack-what-happens-next
Preview meta tags from the blog.redsift.com website.
Linked Hostnames
19- 26 links toredsift.com
- 12 links toblog.redsift.com
- 4 links tothehackernews.com
- 2 links todocs.redsift.com
- 2 links totwitter.com
- 2 links towww.linkedin.com
- 1 link tocareers.redsift.com
- 1 link tocommunity.redsift.com
Thumbnail
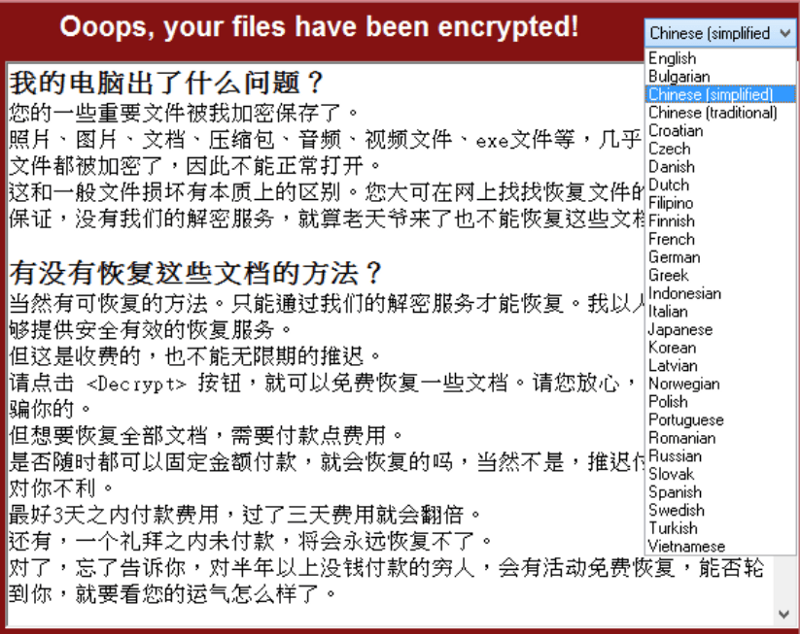
Search Engine Appearance
https://blog.redsift.com/cybersecurity/wannacry-attack-what-happens-next
WannaCry attack: what happens next? - Red Sift Blog
We explore the Wannacry and how we can use these learnings to better prepare our organizations for the next generation of attacks.
Bing
WannaCry attack: what happens next? - Red Sift Blog
https://blog.redsift.com/cybersecurity/wannacry-attack-what-happens-next
We explore the Wannacry and how we can use these learnings to better prepare our organizations for the next generation of attacks.
DuckDuckGo
WannaCry attack: what happens next? - Red Sift Blog
We explore the Wannacry and how we can use these learnings to better prepare our organizations for the next generation of attacks.
General Meta Tags
11- titleWannaCry attack: what happens next? - Red Sift Blog
- viewportwidth=device-width, initial-scale=1.0
- charsetUTF-8
- robotsindex, follow, max-image-preview:large, max-snippet:-1, max-video-preview:-1
- descriptionWe explore the Wannacry and how we can use these learnings to better prepare our organizations for the next generation of attacks.
Open Graph Meta Tags
10og:locale
en_US- og:typearticle
- og:titleWannaCry attack: what happens next? - Red Sift Blog
- og:descriptionWe explore the Wannacry and how we can use these learnings to better prepare our organizations for the next generation of attacks.
- og:urlhttps://blog.redsift.com/cybersecurity/wannacry-attack-what-happens-next/
Twitter Meta Tags
7- twitter:cardsummary_large_image
- twitter:creator@redsift
- twitter:site@redsift
- twitter:label1Written by
- twitter:data1Rahul Powar
Link Tags
27- alternatehttps://blog.redsift.com/wp-json/wp/v2/posts/179
- alternatehttps://blog.redsift.com/wp-json/oembed/1.0/embed?url=https%3A%2F%2Fblog.redsift.com%2Fcybersecurity%2Fwannacry-attack-what-happens-next%2F
- alternatehttps://blog.redsift.com/wp-json/oembed/1.0/embed?url=https%3A%2F%2Fblog.redsift.com%2Fcybersecurity%2Fwannacry-attack-what-happens-next%2F&format=xml
- apple-touch-iconhttps://blog.redsift.com/wp-content/uploads/2018/07/rs-icon-redsift-red-1.png
- canonicalhttps://blog.redsift.com/cybersecurity/wannacry-attack-what-happens-next/
Links
61- http://thehackernews.com/2017/04/window-zero-day-patch.html
- http://thehackernews.com/2017/05/decrypt-jaff-ransomware-files.html
- http://thehackernews.com/2017/05/wannacry-ransomware-cyber-attack.html
- http://thehackernews.com/2017/05/wannacry-ransomware-unlock.html
- http://www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com