blog.sicuranext.com/breaking-down-multipart-parsers-validation-bypass
Preview meta tags from the blog.sicuranext.com website.
Linked Hostnames
13- 10 links toblog.sicuranext.com
- 2 links todatatracker.ietf.org
- 2 links togithub.com
- 1 link toblog.openresty.com
- 1 link tobugs.php.net
- 1 link toen.wikipedia.org
- 1 link toghost.org
- 1 link toopenresty.com
Thumbnail
Search Engine Appearance
Breaking Down Multipart Parsers: File upload validation bypass
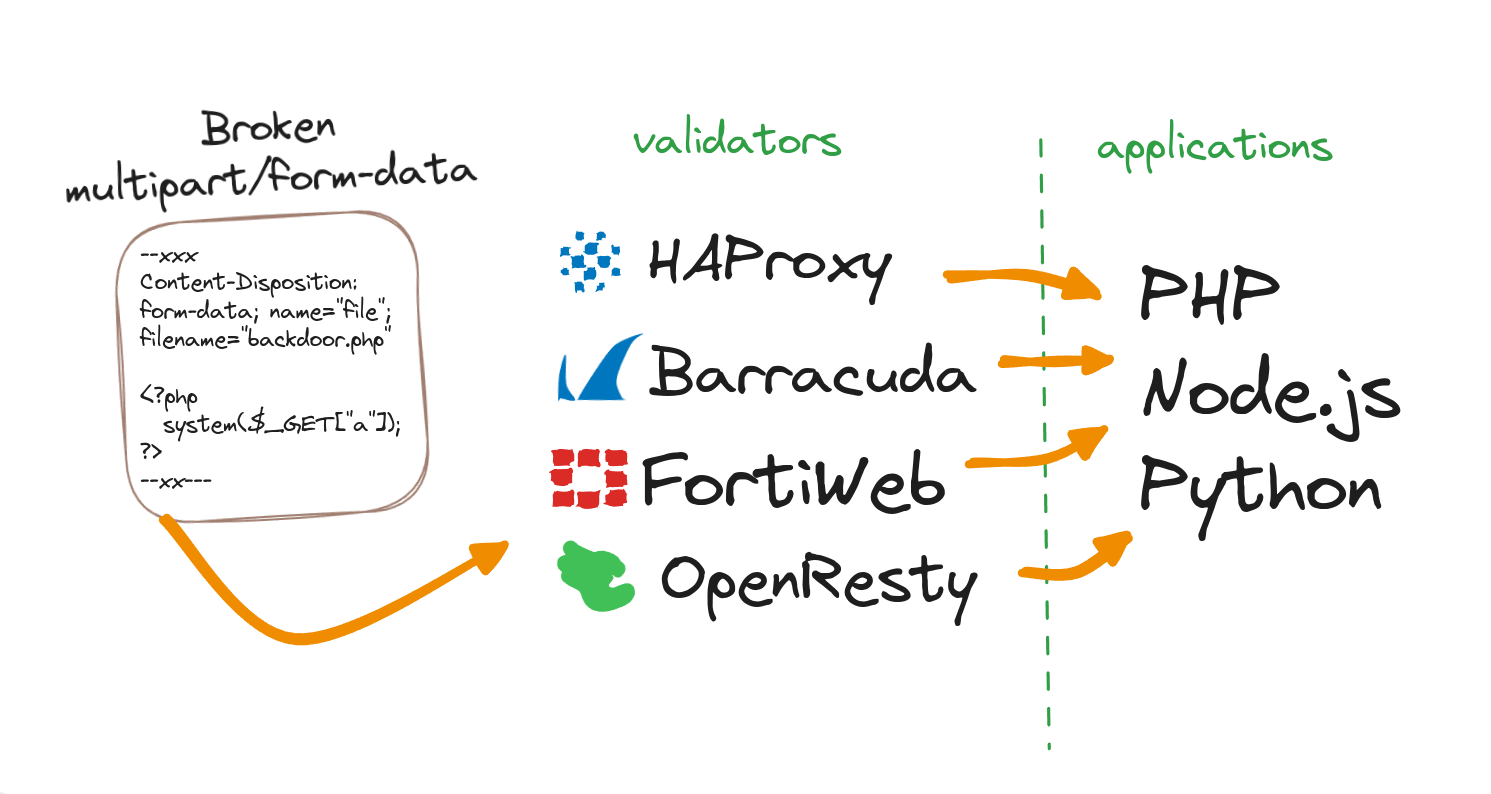
TL;DR: Basically, all multipart/form-data parsers fail to fully comply with the RFC, and when it comes to validating filenames or content uploaded by users, there are always numerous ways to bypass validation. We'll test various bypass techniques against PHP, Node.js, and Python parsers, as well as popular
Bing
Breaking Down Multipart Parsers: File upload validation bypass
TL;DR: Basically, all multipart/form-data parsers fail to fully comply with the RFC, and when it comes to validating filenames or content uploaded by users, there are always numerous ways to bypass validation. We'll test various bypass techniques against PHP, Node.js, and Python parsers, as well as popular
DuckDuckGo
Breaking Down Multipart Parsers: File upload validation bypass
TL;DR: Basically, all multipart/form-data parsers fail to fully comply with the RFC, and when it comes to validating filenames or content uploaded by users, there are always numerous ways to bypass validation. We'll test various bypass techniques against PHP, Node.js, and Python parsers, as well as popular
General Meta Tags
11- titleBreaking Down Multipart Parsers: File upload validation bypass
- charsetutf-8
- X-UA-CompatibleIE=edge
- HandheldFriendlyTrue
- viewportwidth=device-width, initial-scale=1.0
Open Graph Meta Tags
8- og:site_nameSicuranext Blog
- og:typearticle
- og:titleBreaking Down Multipart Parsers: File upload validation bypass
- og:descriptionTL;DR: Basically, all multipart/form-data parsers fail to fully comply with the RFC, and when it comes to validating filenames or content uploaded by users, there are always numerous ways to bypass validation. We'll test various bypass techniques against PHP, Node.js, and Python parsers, as well as popular
- og:urlhttps://blog.sicuranext.com/breaking-down-multipart-parsers-validation-bypass/
Twitter Meta Tags
11- twitter:cardsummary_large_image
- twitter:titleBreaking Down Multipart Parsers: File upload validation bypass
- twitter:descriptionTL;DR: Basically, all multipart/form-data parsers fail to fully comply with the RFC, and when it comes to validating filenames or content uploaded by users, there are always numerous ways to bypass validation. We'll test various bypass techniques against PHP, Node.js, and Python parsers, as well as popular
- twitter:urlhttps://blog.sicuranext.com/breaking-down-multipart-parsers-validation-bypass/
- twitter:imagehttps://blog.sicuranext.com/content/images/2024/10/multipart.png
Link Tags
10- alternatehttps://blog.sicuranext.com/rss/
- canonicalhttps://blog.sicuranext.com/breaking-down-multipart-parsers-validation-bypass/
- iconhttps://blog.sicuranext.com/content/images/size/w256h256/2023/08/favicon.png
- preload/assets/built/screen.css?v=af1b72fe25
- preload/assets/built/casper.js?v=af1b72fe25
Links
24- https://blog.openresty.com/en/edge-enable-waf/?ref=blog.sicuranext.com
- https://blog.sicuranext.com
- https://blog.sicuranext.com/author/themiddle
- https://blog.sicuranext.com/aws-waf-bypass
- https://blog.sicuranext.com/hunt3r-kill3rs-and-the-italian-critical-infrastructure-risks