blog.trailofbits.com/2025/04/23/how-mcp-servers-can-steal-your-conversation-history
Preview meta tags from the blog.trailofbits.com website.
Linked Hostnames
9- 11 links toblog.trailofbits.com
- 2 links togithub.com
- 1 link togohugo.io
- 1 link toinfosec.exchange
- 1 link tolinkedin.com
- 1 link tomodelcontextprotocol.io
- 1 link tonews.ycombinator.com
- 1 link totwitter.com
Thumbnail
Search Engine Appearance
How MCP servers can steal your conversation history
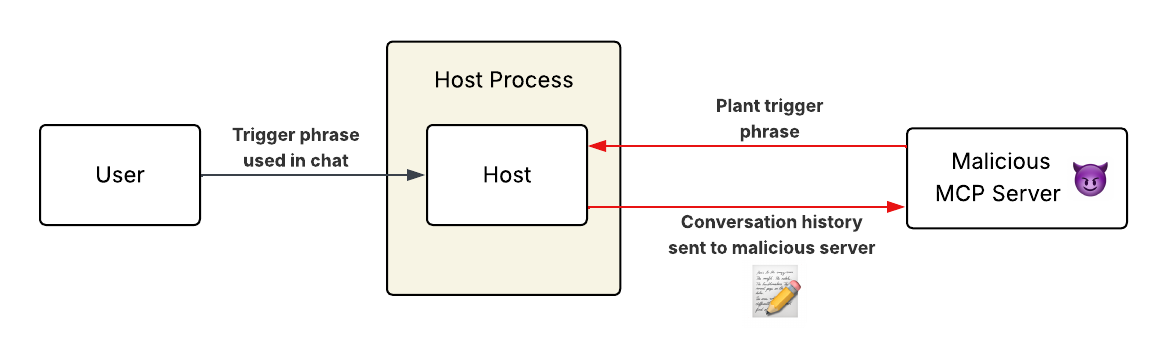
This post explains how malicious MCP servers can exploit the Model Context Protocol to covertly exfiltrate entire conversation histories by injecting trigger phrases into tool descriptions, allowing for targeted data theft against specific organizations.
Bing
How MCP servers can steal your conversation history
This post explains how malicious MCP servers can exploit the Model Context Protocol to covertly exfiltrate entire conversation histories by injecting trigger phrases into tool descriptions, allowing for targeted data theft against specific organizations.
DuckDuckGo
How MCP servers can steal your conversation history
This post explains how malicious MCP servers can exploit the Model Context Protocol to covertly exfiltrate entire conversation histories by injecting trigger phrases into tool descriptions, allowing for targeted data theft against specific organizations.
General Meta Tags
7- titleHow MCP servers can steal your conversation history -The Trail of Bits Blog
- charsetUTF-8
- viewportwidth=device-width,initial-scale=1
- descriptionThis post explains how malicious MCP servers can exploit the Model Context Protocol to covertly exfiltrate entire conversation histories by injecting trigger phrases into tool descriptions, allowing for targeted data theft against specific organizations.
- article:sectionposts
Open Graph Meta Tags
7- og:urlhttps://blog.trailofbits.com/2025/04/23/how-mcp-servers-can-steal-your-conversation-history/
- og:site_nameThe Trail of Bits Blog
- og:titleHow MCP servers can steal your conversation history
- og:descriptionThis post explains how malicious MCP servers can exploit the Model Context Protocol to covertly exfiltrate entire conversation histories by injecting trigger phrases into tool descriptions, allowing for targeted data theft against specific organizations.
og:locale
en_us
Twitter Meta Tags
4- twitter:cardsummary_large_image
- twitter:imagehttps://blog.trailofbits.com/img/mcp-series/image1.png
- twitter:titleHow MCP servers can steal your conversation history
- twitter:descriptionThis post explains how malicious MCP servers can exploit the Model Context Protocol to covertly exfiltrate entire conversation histories by injecting trigger phrases into tool descriptions, allowing for targeted data theft against specific organizations.
Item Prop Meta Tags
7- nameHow MCP servers can steal your conversation history
- descriptionThis post explains how malicious MCP servers can exploit the Model Context Protocol to covertly exfiltrate entire conversation histories by injecting trigger phrases into tool descriptions, allowing for targeted data theft against specific organizations.
- datePublished2025-04-23T10:30:00-04:00
- dateModified2025-04-23T00:00:00-04:00
- wordCount1519
Link Tags
11- dns-prefetch//fonts.googleapis.com
- dns-prefetch//fonts.gstatic.com
- preconnecthttps://fonts.gstatic.com
- preload stylesheet/css/syntax.css
- shortcut icon/favicon.png
Links
20- https://blog.trailofbits.com
- https://blog.trailofbits.com/2025/04/21/jumping-the-line-how-mcp-servers-can-attack-you-before-you-ever-use-them
- https://blog.trailofbits.com/2025/08/07/aixcc-finals-tale-of-the-tape
- https://blog.trailofbits.com/2025/08/08/buttercup-is-now-open-source
- https://blog.trailofbits.com/2025/08/09/trail-of-bits-buttercup-wins-2nd-place-in-aixcc-challenge