blog.trailofbits.com/2025/06/25/maturing-your-smart-contracts-beyond-private-key-risk
Preview meta tags from the blog.trailofbits.com website.
Linked Hostnames
15- 95 links toblog.trailofbits.com
- 2 links togithub.com
- 1 link toblog.solidityscan.com
- 1 link togohugo.io
- 1 link toinfosec.exchange
- 1 link tolearn.bybit.com
- 1 link tolinkedin.com
- 1 link tomedium.com
Thumbnail
Search Engine Appearance
Maturing your smart contracts beyond private key risk
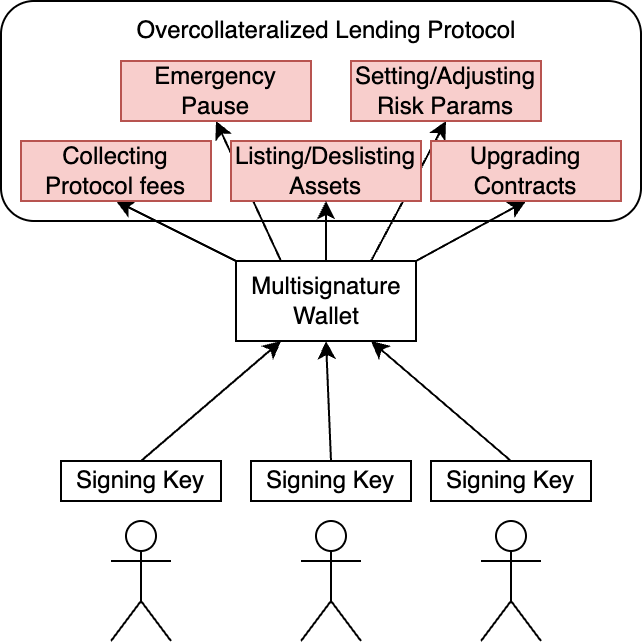
Private key compromise accounted for 43.8% of crypto hacks in 2024, yet traditional smart contract audits rarely address architectural access control weaknesses. This post introduces a four-level maturity framework for designing protocols that can tolerate key compromise, progressing from single EOA control to radical immutability, with practical examples demonstrating multisigs, timelocks, and the principle of least privilege.
Bing
Maturing your smart contracts beyond private key risk
Private key compromise accounted for 43.8% of crypto hacks in 2024, yet traditional smart contract audits rarely address architectural access control weaknesses. This post introduces a four-level maturity framework for designing protocols that can tolerate key compromise, progressing from single EOA control to radical immutability, with practical examples demonstrating multisigs, timelocks, and the principle of least privilege.
DuckDuckGo
Maturing your smart contracts beyond private key risk
Private key compromise accounted for 43.8% of crypto hacks in 2024, yet traditional smart contract audits rarely address architectural access control weaknesses. This post introduces a four-level maturity framework for designing protocols that can tolerate key compromise, progressing from single EOA control to radical immutability, with practical examples demonstrating multisigs, timelocks, and the principle of least privilege.
General Meta Tags
7- titleMaturing your smart contracts beyond private key risk -The Trail of Bits Blog
- charsetUTF-8
- viewportwidth=device-width,initial-scale=1
- descriptionPrivate key compromise accounted for 43.8% of crypto hacks in 2024, yet traditional smart contract audits rarely address architectural access control weaknesses. This post introduces a four-level maturity framework for designing protocols that can tolerate key compromise, progressing from single EOA control to radical immutability, with practical examples demonstrating multisigs, timelocks, and the principle of least privilege.
- article:sectionposts
Open Graph Meta Tags
11- og:urlhttps://blog.trailofbits.com/2025/06/25/maturing-your-smart-contracts-beyond-private-key-risk/
- og:site_nameThe Trail of Bits Blog
- og:titleMaturing your smart contracts beyond private key risk
- og:descriptionPrivate key compromise accounted for 43.8% of crypto hacks in 2024, yet traditional smart contract audits rarely address architectural access control weaknesses. This post introduces a four-level maturity framework for designing protocols that can tolerate key compromise, progressing from single EOA control to radical immutability, with practical examples demonstrating multisigs, timelocks, and the principle of least privilege.
og:locale
en_us
Twitter Meta Tags
4- twitter:cardsummary_large_image
- twitter:imagehttps://blog.trailofbits.com/img/private-key-risk/image1.png
- twitter:titleMaturing your smart contracts beyond private key risk
- twitter:descriptionPrivate key compromise accounted for 43.8% of crypto hacks in 2024, yet traditional smart contract audits rarely address architectural access control weaknesses. This post introduces a four-level maturity framework for designing protocols that can tolerate key compromise, progressing from single EOA control to radical immutability, with practical examples demonstrating multisigs, timelocks, and the principle of least privilege.
Item Prop Meta Tags
11- nameMaturing your smart contracts beyond private key risk
- descriptionPrivate key compromise accounted for 43.8% of crypto hacks in 2024, yet traditional smart contract audits rarely address architectural access control weaknesses. This post introduces a four-level maturity framework for designing protocols that can tolerate key compromise, progressing from single EOA control to radical immutability, with practical examples demonstrating multisigs, timelocks, and the principle of least privilege.
- datePublished2025-06-24T07:00:00-04:00
- dateModified2025-06-25T00:00:00-04:00
- wordCount2534
Link Tags
11- dns-prefetch//fonts.googleapis.com
- dns-prefetch//fonts.gstatic.com
- preconnecthttps://fonts.gstatic.com
- preload stylesheet/css/syntax.css
- shortcut icon/favicon.png
Links
110- https://blog.solidityscan.com/wazirx-hack-analysis-8bc8821928e9
- https://blog.trailofbits.com
- https://blog.trailofbits.com/2025/07/18/building-secure-messaging-is-hard-a-nuanced-take-on-the-bitchat-security-debate
- https://blog.trailofbits.com/2025/07/21/detecting-code-copying-at-scale-with-vendetect
- https://blog.trailofbits.com/2025/07/23/inside-ethcc8-becoming-a-smart-contract-auditor