softwareanalyst.substack.com/p/the-beginners-guide-to-cybersecurity
Preview meta tags from the softwareanalyst.substack.com website.
Linked Hostnames
86- 12 links tosubstack.com
- 8 links tosoftwareanalyst.substack.com
- 8 links tosubstackcdn.com
- 6 links towww.cloudflare.com
- 4 links towww.gartner.com
- 3 links towww.crowdstrike.com
- 3 links towww.fortinet.com
- 2 links tomaven.com
Thumbnail
Search Engine Appearance
https://softwareanalyst.substack.com/p/the-beginners-guide-to-cybersecurity
The Beginner's Guide to Cybersecurity
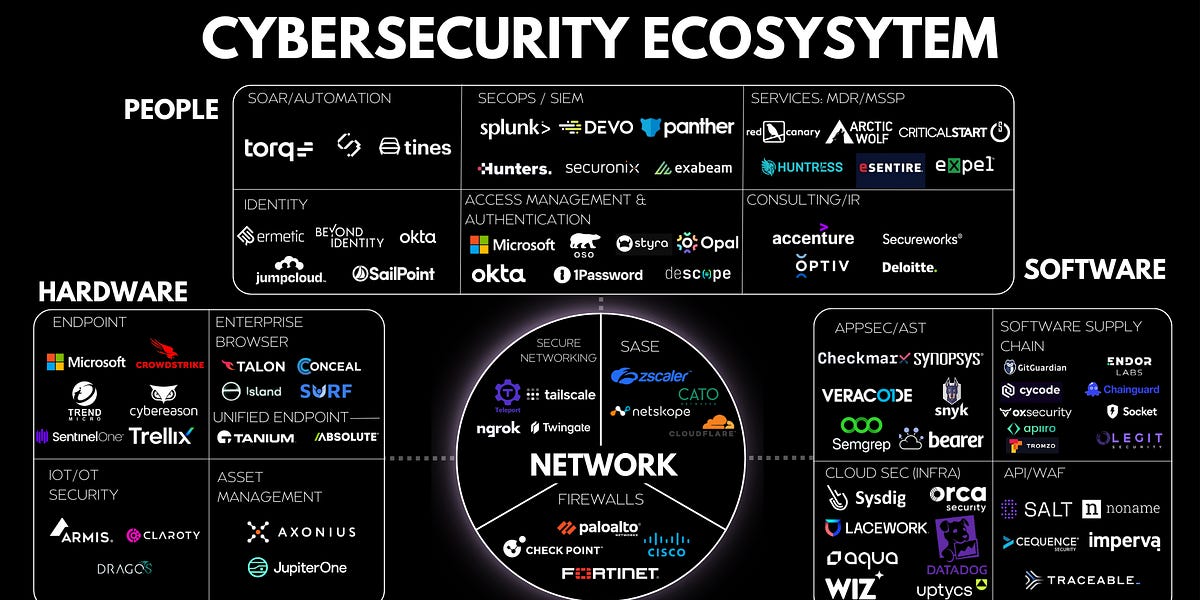
A simple framework for synthesizing the cybersecurity industry and its 3500 vendors.
Bing
The Beginner's Guide to Cybersecurity
https://softwareanalyst.substack.com/p/the-beginners-guide-to-cybersecurity
A simple framework for synthesizing the cybersecurity industry and its 3500 vendors.
DuckDuckGo
The Beginner's Guide to Cybersecurity
A simple framework for synthesizing the cybersecurity industry and its 3500 vendors.
General Meta Tags
30- titleThe Beginner's Guide to Cybersecurity - by Francis Odum
- title
- title
- title
- title
Open Graph Meta Tags
5- og:urlhttps://softwareanalyst.substack.com/p/the-beginners-guide-to-cybersecurity
- og:typearticle
- og:titleThe Beginner's Guide to Cybersecurity
- og:descriptionA simple framework for synthesizing the cybersecurity industry and its 3500 vendors.
- og:imagehttps://substackcdn.com/image/fetch/$s_!CGD1!,w_1200,h_600,c_fill,f_jpg,q_auto:good,fl_progressive:steep,g_auto/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2F3c8f1ed0-ef70-48f6-93fc-800e167ad5d5_2245x1587.png
Twitter Meta Tags
4- twitter:titleThe Beginner's Guide to Cybersecurity
- twitter:descriptionA simple framework for synthesizing the cybersecurity industry and its 3500 vendors.
- twitter:imagehttps://substackcdn.com/image/fetch/$s_!s6NE!,f_auto,q_auto:best,fl_progressive:steep/https%3A%2F%2Fsoftwareanalyst.substack.com%2Fapi%2Fv1%2Fpost_preview%2F136148236%2Ftwitter.jpg%3Fversion%3D4
- twitter:cardsummary_large_image
Link Tags
32- alternate/feed
- apple-touch-iconhttps://substackcdn.com/image/fetch/$s_!78xZ!,f_auto,q_auto:good,fl_progressive:steep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2Fc4133308-e8b4-425b-99a5-7834330ebe34%2Fapple-touch-icon-57x57.png
- apple-touch-iconhttps://substackcdn.com/image/fetch/$s_!UqVn!,f_auto,q_auto:good,fl_progressive:steep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2Fc4133308-e8b4-425b-99a5-7834330ebe34%2Fapple-touch-icon-60x60.png
- apple-touch-iconhttps://substackcdn.com/image/fetch/$s_!ajz7!,f_auto,q_auto:good,fl_progressive:steep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2Fc4133308-e8b4-425b-99a5-7834330ebe34%2Fapple-touch-icon-72x72.png
- apple-touch-iconhttps://substackcdn.com/image/fetch/$s_!rJG9!,f_auto,q_auto:good,fl_progressive:steep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2Fc4133308-e8b4-425b-99a5-7834330ebe34%2Fapple-touch-icon-76x76.png
Links
131- https://abnormalsecurity.com/blog/key-takeaways-gartner-market-guide
- https://blogs.gartner.com/andrew-lerner/2019/12/23/say-hello-sase-secure-access-service-edge
- https://cloudsmith.com/?ref=strategyofsecurity.com
- https://conceal.io
- https://cyware.com/?ref=strategyofsecurity.com